If a Payment Is Pending How Does It Read on a Ledger
Ledger 101 — Part 3: Best Practices When Using a Hardware Wallet
![]()

The previous instalments of the Ledger 101 series have shown the necessity of using a hardware wallet as well as the importance of using secure fries to build them.
Hardware wallets empower you lot with the ownership and control of your crypto assets. But with great powers comes great responsibilities: being your own bank is certainly not trivial and requires subject. Using a hardware wallet doesn't brand yous invincible against social engineering, physical threats or man errors. Y'all must always use common sense, and employ basic security principles.
There are five basic golden rules
- Never ever share your 24-word recovery phrase, in whatever grade, with anyone.
- Never ever store your recovery phrase on a computer or smartphone.
- Keep your Recovery sheet physically secure to make certain you lot can't lose or destroy information technology by accident.
- Only trust what you can come across on your hardware wallet screen. Verify your receiving accost and payment information on your device.
- Ever treat information shown on your computer or smartphone screen with caution. Assume that software can get compromised anytime.
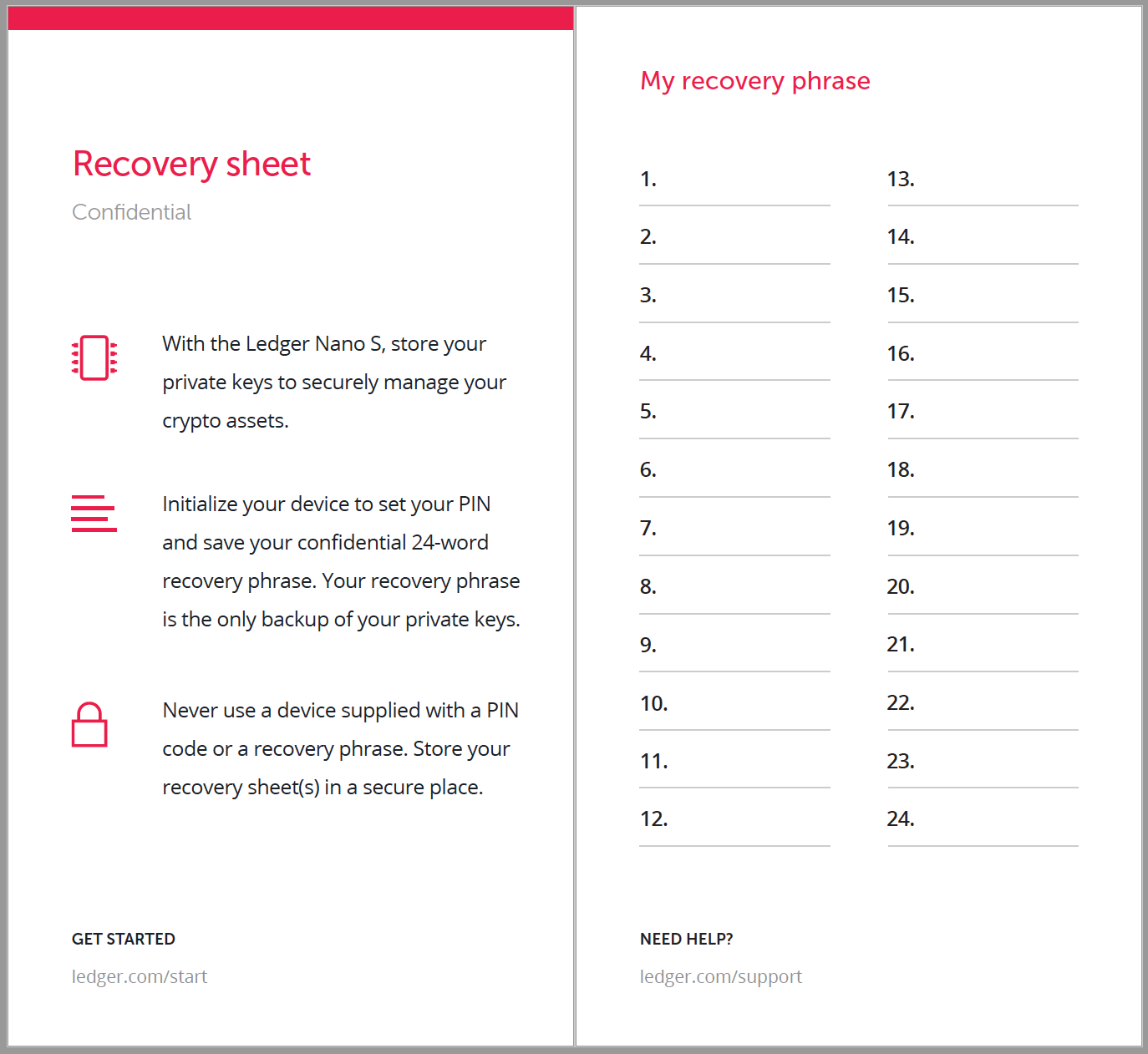
The 24-word recovery phrase
When initiali z ing your hardware wallet for the starting time time, you volition be prompted to write down 24 words on a Recovery sheet. These 24 words are called a recovery phrase and are a human readable back-up from which all your private keys are derived. They are used to restore access to your crypto assets on another Ledger device or any other compatible wallet.
General security principles
There are 2 basic reasons why yous would need access to your recovery phrase:
- Loss or destruction of your hardware wallet: you tin can enter your recovery phrase on a new device to recover full access to your crypto assets;
- Cloning to a new device: by entering your 24 words on another device, you'll be in possession of 2 hardware wallets yous can employ independently. For instance, one at the office and one at your house, preventing you from having to transport information technology all the fourth dimension. Another reason to clone a device would be when upgrading to a newer model.
As you can hands deduct from this, anyone getting admission to these 24 words would get immediate access to your crypto assets. The Pin code on your hardware wallet is a protection related merely to your device, and is totally unnecessary for private keys recovery.
Therefore, it is of the utmost importance that your recovery stage is correctly secured. Any compromise, at any fourth dimension, could lead to catastrophic losses;
- Never take a picture of your Recovery sheet. Your smartphone is not safe and, worse, information technology could get automatically uploaded to your deject storage;
- Never enter your recovery phrase on any computer or smartphone: you could take keyloggers, and storing this information online (even encrypted) completely defeats the purpose of using a hardware wallet;
- Never show or share your 24 words to anyone (including friends and family unit). If you practice decide to share, be fully aware that they take potential access to all your crypto assets, anytime, and without an piece of cake way of revoking access;
- Keep your Recovery sheet in a safe place, protected from sunlight, humidity and burn down. If it gets destroyed for whatever reason, you must immediately motility your crypto to a newly set hardware wallet;
Additionally, it is critical to brand sure that y'all accept generated the 24-give-and-take recovery phrase yourself. Never, ever, utilize a preconfigured device. Never, e'er, employ a set of 24 words provided anywhere else than on the device itself. You must ensure you are the only one in the globe to have knowledge of this specific recovery phrase.
As the availability of your recovery phrase is critical, you may wish to verify that you've indeed written it downward correctly and that you tin can actually read it without error. For a Ledger Nano S, y'all can verify this with the Recovery Check app. This app lets you lot enter your 24-word recovery phrase and checks whether it matches the private keys on your device. Please refer to the dedicated video for more data.
General safety principles
Having a hardware wallet set upwards with a verified backup in a secure place may protect you from a digital attack, but yous are still vulnerable to potential physical threats such every bit a burglary or a hostage situation. This is why you must follow these basic rules:
- Never tell anyone that y'all own cryptocurrencies. If you exercise, make sure to go along the real value of your assets to yourself. If people inquire you lot how many bitcoins yous own, simply return the question by asking dorsum how many euros/dollars they own;
- If yous are active in the online cryptocurrency community, protect your real identity and always be mindful of the information you share. Yous don't desire to become the target of a heist;
- Exercise not keep your Recovery canvas in a prophylactic at dwelling. A bank vault is much more secure. Non having immediate access to your backup increases your resilience to physical threats;
- If you have big amounts of cryptocurrencies that you lot do non demand frequent access to, keep your hardware wallet in the bank safe equally well. You can use another hardware wallet with lower amounts for frequent employ;
Only trust your hardware wallet
Your hardware wallet requires a companion app to interact with you and to access the cyberspace, so you can check your remainder on your computer, get your transaction history, and broadcast new transactions. Ledger Alive is Ledger's own awarding available for PC, Mac and Linux. Ledger devices besides work with applications that are non made by Ledger.
In principle, information technology is very difficult to verify the integrity of the software on your computer. You must therefore assume that your computer is compromised and that what you run across on your screen could be manipulated.
Yous tin can only trust your hardware wallet.
Security steps to verify your receiving address
When you need to share your receiving address so yous can be the recipient of a payment, you must take actress precautions to ensure you don't fall victim to a man in the middle assault. An aggressor in control of your computer screen could show yous a incorrect address which would make him the beneficiary of any transaction sent to it.
Yous must verify the receive address shown on your screen by displaying it on your device.
When requesting a receiving address on Ledger Alive, you are prompted to connect your hardware wallet and open up the corresponding app. The address will then be shown on the secure display of the device and y'all'll be able to verify that it matches the one on your screen.
If yous're using the QR code to transmit the accost, brand sure to verify the address after scanning it.
If you are using a software wallet without this feature (many third party applications are compatible with Ledger devices), we recommend sending a minor amount starting time, to make sure that you have properly received it. This test should ideally be done on another estimator. You can reuse the address that y'all accept simply verified for the test.
Security steps to verify the beneficiary accost
When you wish to send a transaction, you volition usually go the recipient address on a web folio or through a communication service. A niggling attack for a malware would be to replace this accost by one of its own. Some malicious pieces of software are merely monitoring the clipboard to supervene upon the address you take just copied by one belonging to the attacker.
To foreclose falling victim to this attack, always verify the beneficiary address on the device before approval the transaction, and likewise always double check it using a second communication channel. For example, asking the address to exist sent by SMS, or another messaging app then you tin verify it. If you lot are depositing to an exchange, first send a small amount and check that it has arrived properly before sending larger amounts.
Existence your own bank is not trivial and requires discipline. Having a hardware wallet does non make you invincible. Just we hope these security tips assist you protect yourself while using them.
As always, use common sense. Don't trust, verify.
Source: https://medium.com/@ericlarch/ledger-101-part-3-best-practices-when-using-a-hardware-wallet-198b60df2681
0 Response to "If a Payment Is Pending How Does It Read on a Ledger"
Post a Comment